Developing secure financial software requires a significant investment of time and money. However, not caring about safety issues can cost you even more.
The good news is that with the right team of people who possess relevant experience and knowledge of key industry requirements you can develop a bulletproof solution without throwing away your resources.
Modern FinTech Risks and Challenges
Fintech development is like an arms race between creators and those who want to benefit from apps’ vulnerability. With the development of new security features new tricks arise to break them.
Today’s challenges may differ significantly from those we had a few years ago, so it’s important to keep an ear to the ground. Below are a few of the most typical challenges faced by financial businesses worldwide.
1. Data ownership and identity management
Data sharing is the lifeblood of any fintech app, but there's one hitch.
Fintech providers store gigabytes of user data, but what happens to that data when a user quits the service and deletes an account? Companies are required to integrate effective mechanisms to erase such data from their storage, but what if they don't and the data gets stolen? Ooops...
2. Data protection
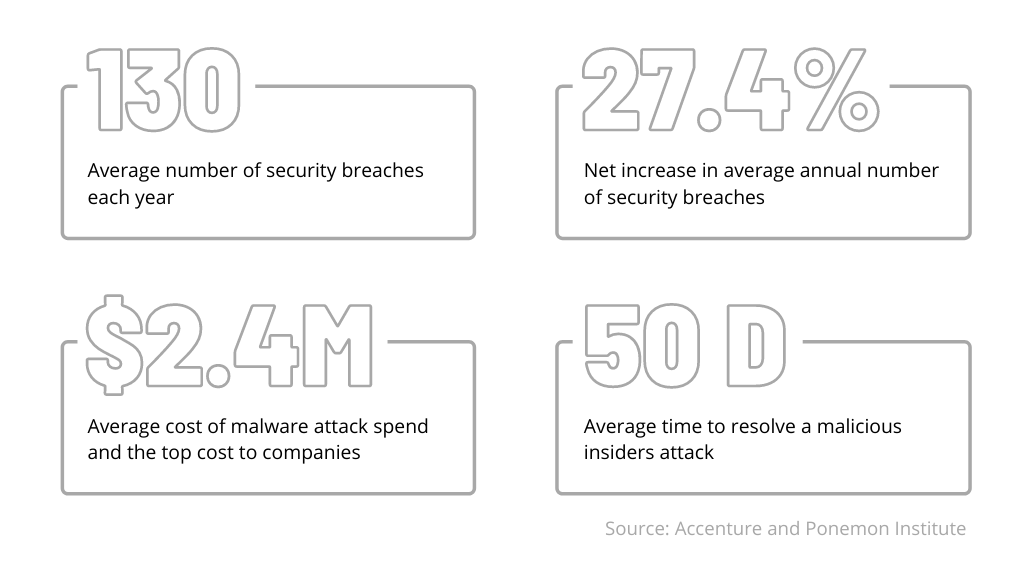
Today, data security is a hotter issues than ever before. According to the Accenture and Ponemon Institute Study, US capital market firms and banks spent an average of $11.7 million to fight cybercrime in 2020, which is 23% more than they spent in 2019. However, these measures are not always enough. Over the last few years, the annual number of breaches has increased 27.4%. The cost of failure has also increased. A successful attack can result in a loss of over $2,4M and take up to 50 days to resolve.
But the worst part is that most organizations don’t know about the breaches until it’s too late. Bitdefender’s survey showed that 64% of companies didn't even notice their system was attacked.
3. Local requirements
Fintech products must follow regional data protection regulations. For example, if you act within the EU, you are obliged to follow GDPR. At the same time, you shouldn't forget about your Japanese clients and APPI, etc.
The point is that every regional privacy act can limit the data you can collect. Some may also oblige you to store such data and share it with the government. In addition, different regions can interpret the same legislative concepts in a different way, and you need to know all of these nuances. Otherwise, some markets will stay closed to you.
Here are a few of the most common regulations you should be aware of:
- GDPR – A set of requirements tailored to protect the personal data of EU residents, but not only European companies should follow it. If you plan to act in the European Union’s market, you should comply with it.
- PSD2 – An updated payment services directive that regulates e-payments within the EU.
- eIDAS - Another EU regulation for cross-border electronic transactions.
- FCA – This regulation was created to control financial services within the UK. All providers should complete a registration process to enter the market.
- GPG13 – Her majesty’s security protocol. It involves service providers and outsourcing companies working with the UK’s governmental system.
- APPI – The Japanese analog of GDPR. It protects Japanese residents’ user data and applies to all providers operating in the country.
- PIPA – This act regulates private data protection measures in South Korea. PIPA violators can face penalties and even criminal liability.
- PCI DSS – Covers all entities that collect, process, and use credit card information. There are four PCI DSS levels. The more transactions you service annually, the stricter the rules you have to obey.
- ISO/IEC 27001 – A set of cybersecurity standards that include cryptography, access control, clear screen, and data protection. It was created to help businesses all around the world develop secure data management systems.
FinTech Cybersecurity Must-Haves
Businesses that care about their users and their reputation should pay special attention to data security and apply the latest techniques to ensure high-end protection.
Here are a few of the best practices we utilize in our development process and suggest to everyone who wants to create secure fintech solutions.
Encryption and tokenization
Encryption means encoding data into a set of symbols that require a special key to be decoded back into their initial format. As of today, there are a few widely used methods to encrypt your data safely.
- RSA – a bulletproof asymmetric algorithm with public and private keys.
- Twofish - a freeware algorithm that encodes data into 128-bit blocks.
- Triple DES (3DES) – this algorithm breaks data into 64-bit blocks and encrypts each one three times; an optimal method to protect credit card PINs.
Tokenization means replacing private information with a generated number (token). You can get the original information by using special databases (token vaults).
Both methods have proven their efficiency, but simply being efficient isn’t enough for us, is it? You can mix these methods and encrypt a token vault to acheive ultimate security.
Role-based access control (RBAC)
The core idea of this method is allowing or restricting access to specific parts of your system based on a user’s position.
For example, you can divide users into the following categories:
- Admin
- Manager
- IT specialist/System administrator
- Support specialist
- Customer
By implementing access levels, you can prevent your ordinary employees and clients from accessing sensitive data. Thus, you minimize the vulnerability of your system to both external and internal threats.
Secure authentication
A strict password policy is fundamental for financial software security, but it is not enough to ensure 100% safety—just like a foundation is critical for your home’s future sustainability but is not enough to shelter you from inclement weather.

To secure your system, you need to add extra layers of protection to password access:
- One-Time Password. The application generates a temporary password every time a client wants to access an account or make a transaction.
- Regular password update. Most attacks happen due to password compromises. To minimize potential losses, you can force your users to change their passwords every 3-6 months.
- Tracking system. You can monitor and detect suspicious user behavior, such as failed log-ins or anomalous transactions. By blocking suspicious accounts, you can prevent potential data breaches.
- Reduced session time. By limiting a log-in session, you can limit the time an attacker interacts with a compromised account.
- Adaptive authentication. 2FA is not enough to protect an account. In fact, it can help attackers who have a user’s phone or its clone. Adaptive authentication analyzes user behavior and reacts to suspicious actions.
Multi-cloud data storage
A public cloud storage system cannot provide desired security for a fintech solution. At the same time, a private cloud can limit potential users’ access to your solution, thus becoming a bottleneck to future growth. Multi-cloud solutions can deliver the best of both worlds. They give businesses greater transparency along with security and regular backups for sensitive information.
DevSecOps
Cyber security should be a never-ending process and an integral part of the development lifecycle. Like we said before, new threats arise every day, so it’s important to continually improve your protection. The DevSecOps methodology is a great solution to achieve this goal.
Penetration testing
Penetration testing means simulating false attacks on your system to find potential vulnerabilities and fix them before someone else finds a way to abuse them.
You can either create an in-house team for this purpose or hire a company that offers penetration testing services.
It’s important to run tests regularly and make them a part of your development process. Otherwise, you risk missing a technological flaw that may cost you millions later.
Educate your team
Humans are the weakest link in the information security chain; every cyber expert can prove it. The lion’s share of successful attacks are of the phishing and social engineering variety.
That’s why it’s important to teach your staff to detect and avoid such attempts, or one day you may find your user database being shared over the dark net just because your accountant turned out to be an heir to a Nigerian billionaire.
Check out a related article:
Remote Work Security Risks and 6 Tips on How to Avoid Them
How can we help you?
Intersog specializes in both domains: fintech application development and cybersecurity consultancy. Thus, we can offer both of these services under one roof.
Our team will integrate security features as early as possible and run regular tests with each update. Thus, we can minimize the number of future bugs and vulnerabilities and deliver a solution that your clients can rely on.
Feel free to contact us for more details.
Leave a Comment