Challenge
Cloud storage solutions allow businesses to substantially decrease expenses and flexibly allocate resources. The expansion of cloud-adoption along with the propagation of BYOD helped many businesses accelerate their growth, but at the same time created new risks to their security.
This has formed a new demand for safer, more reliable, authorized apps like Office 365, DropBox, Salesforce, etc.
In addition, workers themselves can be a weak point of company security. Malicious insiders can easily benefit from unlimited access to internal enterprise data, while other, non-malicious employees may not be that careful with the security of their accounts. So are some of the partners and clients. As a result, stolen accounts due to credentials takeover is one of the most critical issues of cloud-based solutions.
To address the above problems, the Client has hired Intersog to engineer a secure Cloud Gateway solution.
Solution
Intersog was selected out of many other software development services providers, due to optimal value proposition and ability to provide an experienced offshore team within the shortest time and with no HR and management hassle from their side.
Having started with one junior software developer, the customer has quickly scaled the agile team to seventeen specialists.
Today, the team includes the following roles:
- Software development engineers
- UX / UI designers
- manual and automation QA specialists
- data miners
- business analysts
- Cloud engineers, etc
Results
A Cloud Gateway developed by our engineers facilitates examination of Cloud applications use, assess risks, and provides proper controls for SaaS and data-sharing apps.
How it works:
1) Data Leak Prevention
The system controls storage and transfer of sensitive and confidential information.
2) User Monitoring
Monitors real-time activity and notifies admins about anomalies in user behavior.
3)Cyber Threat Prevention
Detects, alerts, and blocks require an identity verification for suspicious actions.
Below you'll find an illustration of the systems regular workflow:
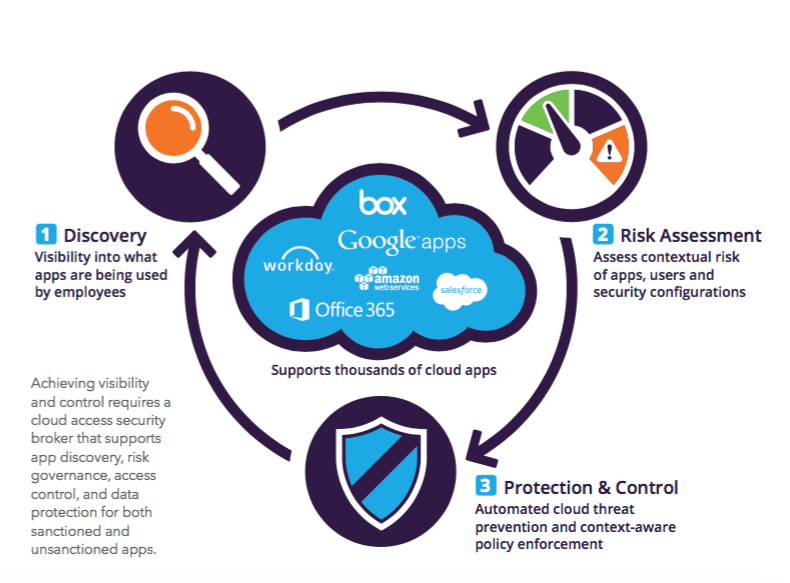
Data analytics functions of the system include:
- SaaS services data review
- Identification of client needs
- Analysis of incoming data:
- Data hosting & provider
- Authentication types
- Used URLs & IP addresses
- Security standards compliances
- Backdoors
- Storage and analysis of data to gain useful insights and patterns.
We still cooperate with the client and keep updating and supporting the innovative cloud solution.


