Over the past 12 months, the financial sector has witnessed a series of breaches that would have seemed improbable only a few years ago. In 2024, ransomware crews hit mortgage lender LoanDepot and Evolve Bank & Trust, encrypting systems and stealing data on nearly 17 million people after an employee clicked on a malicious link. In early 2025, a supply-chain attack on Santander and DBS Bank took advantage of third-party providers - the printing vendor Toppan Next Tech was compromised by ransomware - and led to the leak of over 8,000 customer records and employee data from multiple countries. These stories highlight a common theme: attackers don't need to break your code when they can exploit a weak link in your ecosystem or trick a member of staff into opening the door.
At the same time, regulators have raised the bar dramatically. The EU’s Digital Operational Resilience Act (DORA), which came into effect on 17 January 2025, harmonises operational resilience rules for banks, insurers, and other financial institutions across the EU. It requires these institutions to manage ICT risks, test their resilience, and supervise critical third-party providers. The 47 new requirements of PCI DSS 4.0 became mandatory after 31 March 2025, introducing stronger anti-malware controls, the encrypted storage of sensitive authentication data, and stricter authentication rules. ISO 27001:2022 reduced the number of controls from 114 to 93, introducing 11 new controls (e.g. threat intelligence and information security for cloud services), with a transition deadline of 31 October 2025. NIST’s Cybersecurity Framework 2.0 now applies to all organisations, adding a new 'Govern' function to emphasise governance and supply-chain risk. In Israel, Amendment 13 to the Privacy Protection Law was approved in August 2024 and will take effect on 14 August 2025. It expands data definitions, requires many organisations to appoint a Privacy Protection Officer (PPO) and mandates formal risk assessments, penetration tests and strict vendor oversight.
The message for founders, CTOs and CISOs building fintechs in 2025 is clear: security cannot be an afterthought. This playbook translates the jargon of PCI DSS 4.0, DORA, ISO 27001:2022, NIST CSF 2.0, GDPR and Israeli regulations into practical protocols and controls. It provides a roadmap for progressing from a minimum viable product to bank-grade security, combining compliance with practical measures such as OAuth 2.1, OpenID Connect, Financial-grade API (FAPI 2.0), mutual TLS (mTLS), tokenisation, WebAuthn, zero trust, and secrets management. Tables and checklists wherever possible help you prioritise what to implement and when.
Threats that actually hit fintechs

Account takeover, phishing and credential stuffing
Account Takeover (ATO) remains one of the fastest-growing threats. According to Sift's Q3 2025 Digital Trust Index, 83% of organisations experienced at least one ATO incident in 2024–25. Losses from ATO fraud are projected to reach $17 billion in 2025, up from $13 billion the previous year. The overall ATO attack rate increased to 2.5% in Q2 2025, with fintech-specific attacks surging by 122% year-on-year. Attackers harvest credentials through data breaches, phishing and malware, and then use bots to automate login attempts. Stolen credentials are often reused across multiple sites. The human element remains the weakest link. Verizon's 2025 Data Breach Investigations Report revealed that 68% of breaches involve individuals clicking on malicious links or misconfiguring systems.
API abuse and supply‑chain compromise
Fintechs expose many interfaces, such as mobile and web apps and partner APIs, and attackers often exploit these endpoints. Ransomware and data exfiltration groups are increasingly targeting third-party providers in order to access financial institutions. Supply-chain attacks on Santander and DBS Bank, for example, demonstrate how ransomware at a printing vendor can lead to the leakage of customer and employee data. Attackers also compromise cloud hosting providers or API management platforms to intercept tokens or inject malicious code.
Synthetic identities, card‑not‑present fraud and insider threats
The rise of AI‑generated content makes it trivial to create synthetic identities combining real and fabricated data. Fraudsters open accounts with stolen credentials, bypass identity checks and then launder funds or apply for loans. Card‑not‑present transactions and stored payment details on mobile wallets present ripe targets: the Fintech Fraud Industry Benchmarking Resource shows payment fraud rates hovering around 3.5 %, while chargebacks declined but ATO attacks increased. Malicious insiders also pose a serious risk; in early 2025 a former employee of the U.S. Consumer Financial Protection Bureau forwarded confidential information on 256 000 consumers and 45 financial institutions to their personal email. Even the best perimeter controls can’t stop an authorised user from misusing data.
Mobile app reverse engineering and malware
An increasing number of fintech users prefer mobile apps. However, attackers can decompile apps, insert malicious code and bypass certificate checks, or even intercept API requests. On jailbroken devices, Trojan malware can harvest session tokens, and fraudsters can deploy bots to simulate legitimate user behaviour. Without proper runtime protections and certificate pinning, client-side code can easily be used to access your backend.
Protocols that matter (and when to use them)
Many fintechs get lost in a maze of acronyms. This section lists protocols and controls that materially reduce risk in 2025, along with where to deploy them, common pitfalls and a quick test of adequacy.
Authentication & session management
WebAuthn/FIDO2 and passkeys – Passkeys are FIDO credentials that use asymmetric cryptography to replace passwords. A passkey comprises a public/private key pair that is stored on the user's device. Authentication occurs locally and the private key never leaves the device. According to the FIDO Alliance, passkeys improve sign-in success, reduce phishing and credential-stuffing attacks, and lower password-reset costs. Biometric data (e.g. fingerprints or facial recognition) is stored on the device and is only used to unlock the private key.
Where to use: high‑risk flows such as account creation, adding beneficiaries and confirming large transactions.
Pitfalls: require modern devices and browser support; back‑up keys and account recovery flows must be robust.
Quick test: does your sign‑in flow support passwordless logins using WebAuthn and issue bound tokens (e.g., DPoP or mTLS) for session management?
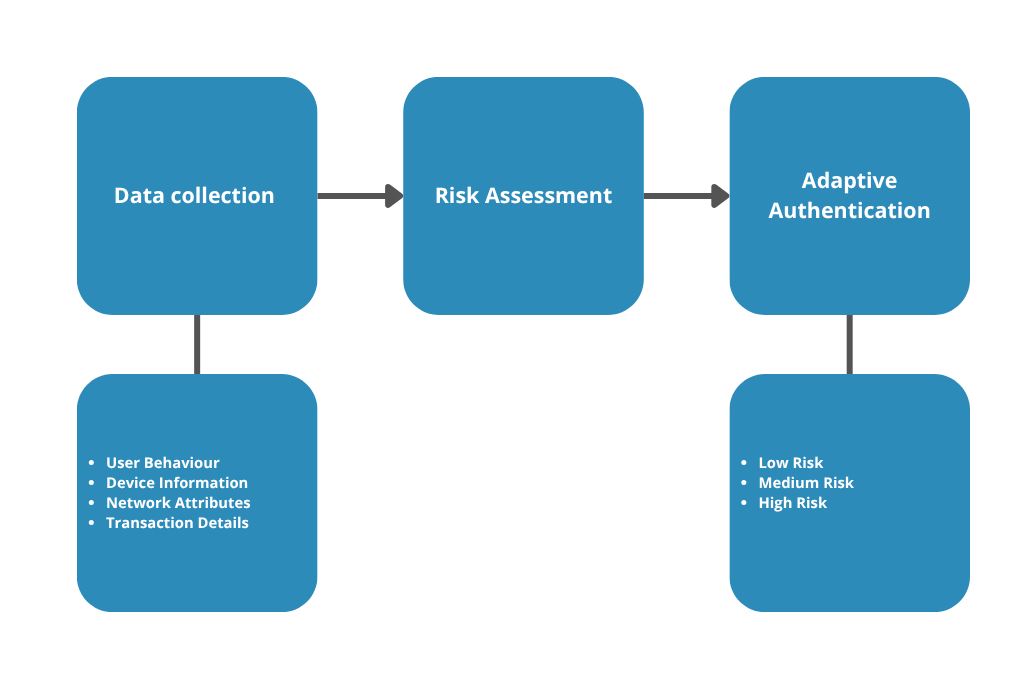
Multi‑factor & risk‑based authentication (RBA) – Risk-based authentication collects user behaviour data, such as location, device attributes and transaction context, to calculate a risk score and adjust authentication requirements accordingly. According to SuperTokens, RBA enhances security by triggering additional verification only when the risk level is high, thereby improving both user experience and fraud prevention. Device fingerprinting gathers information such as time zone, screen resolution, and browser features to create identifiers that help to detect anomalies. RBA often uses behavioural biometrics, such as typing patterns or swipe gestures, to differentiate between legitimate and unauthorised users.
Where to use: login, transaction initiation and password resets.
Pitfalls: privacy concerns and data protection obligations; false positives causing friction.
Quick test: do you evaluate risk per session and adaptively challenge only when risk scores exceed thresholds?
Session security – Use short-lived access tokens alongside refresh token rotation. OAuth 2.1 requires Proof Key for Code Exchange (PKCE) for all authorisation code flows and removes the implicit grant. It also requires exact redirect URI matching and discourages bearer tokens in query strings. For public clients, refresh tokens must either be sender-constrained (e.g. mTLS or DPoP), or be for single use only. The FAPI 2.0 security profile requires Pushed Authorisation Requests (PAR) and Demonstration of Proof of Possession (DPoP) tokens, moving away from front-channel request parameters and strengthening client authentication.
Where to use: any open banking or consent‑driven API flows.
Pitfalls: misconfigured redirect URIs, reusing tokens across sessions, neglecting client authentication.
Quick test: do you use PKCE by default, enforce strict redirect URI matching and bind refresh tokens to client keys?
Authorization for APIs
OAuth 2.1 + OpenID Connect – OpenID Connect is an identity layer built on top of OAuth 2.0, which returns a JWT (JSON Web Token) to authenticate a user. Use OIDC to verify the user's identity and OAuth scopes to authorise API calls. Avoid the 'resource owner password credentials' grant and the 'implicit' grant (both of which were removed in OAuth 2.1).
Where to use: any user‑facing API requiring login.
Pitfalls: storing ID tokens without verifying signatures; not validating aud (audience) and exp claims.
Quick test: is your API using authorization code flow with PKCE and exchanging an ID token in the back‑end only?
FAPI 2.0 (Financial‑grade API) – FAPI 2.0 направлен на упрощение и усиление безопасности API для данных, имеющих высокую ценность. Необходимые элементы включают в себя запросы на авторизацию с отправкой, JWT с закрытым ключом или взаимный TLS (mTLS) для аутентификации клиента, токены с ограничением отправителя через mTLS или DPoP, а также опциональный JWE для шифрования переднего канала. FAPI делает акцент на запросах на расширенную авторизацию (RAR) для передачи сведений о согласии пользователя и моделей атак для оценки безопасности.
Where to use: open banking, PSD3/OBIE integration, and any regulated API sharing sensitive financial data.
Pitfalls: increased complexity; requires careful key management and certificate handling.
Quick test: do your authorization requests use the PAR endpoint, are client credentials bound via mTLS, and are tokens proof‑of‑possession?
mTLS and DPoP – mTLS (mutual TLS) requires both client and server to present certificates, enabling strong client authentication and token binding. DPoP uses a public/private key pair to sign HTTP requests, proving possession of the private key when presenting tokens. FAPI 2.0 mandates at least one of these methods.
Where to use: internal service‑to‑service calls, token exchange, and high‑risk API endpoints.
Pitfalls: managing certificate issuance and rotation; mismatching TLS versions.
Quick test: are all internal service calls protected by mTLS or DPoP? Are certificates rotated regularly?
JWT/JWS hardening – Ensure that JSON Web Tokens are signed using strong algorithms (RS256 or ES256) and include expiration (exp), issuer (iss), audience (aud) and subject (sub) claims. Avoid using none or symmetric algorithms for tokens that leave your domain. Implement key rotation and verify tokens at each hop.
Transport & data protection
TLS 1.2/1.3 and modern ciphers – Use TLS 1.2 or 1.3 with secure cipher suites (e.g., AES‑GCM, ChaCha20‑Poly1305) and disable outdated ciphers. For internal traffic use mTLS. Enforce HTTP Strict Transport Security (HSTS) and certificate pinning sparingly - OWASP warns that pinning is rarely necessary and can cause outages; only pin if you control both client and server and provide backup pins for rotation.
Tokenisation and encryption – Stripe explains that tokenisation involves replacing sensitive data, such as credit card numbers, with meaningless tokens that are stored in a secure vault. This makes the tokens irreversible without access to the vault. In contrast, encryption transforms plaintext into ciphertext using a key. This process is reversible and is used to protect data at rest and in transit. Comparing the two techniques shows that, while encryption alters the data structure and is reversible with the correct key, tokenisation preserves the data format and is irreversible without access to the vault. Format-preserving encryption (FPE) retains the original length and format of the data, which is useful when legacy systems require the same structure. It also allows you to search and sort encrypted data.
Where to use: tokenise PANs (primary account numbers), national IDs and other high‑value fields in storage; encrypt database backups and communication channels; use FPE when field format must remain unchanged.
Pitfalls: storing encryption keys with encrypted data; failing to rotate keys; using reversible encryption when tokenisation is mandated.
Quick test: are sensitive fields tokenised in the data store? Is encryption used for backups, logs and API calls?
Key management systems (KMS) & hardware security modules (HSMs) – Secure key management is vital. Сryptography requires keys and that managing these keys throughout their entire lifecycle — generation, usage, rotation and destruction — is mandated by standards such as PCI DSS, HIPAA, GDPR and ISO 27001. Hardware Security Modules (HSMs) generate and store keys in tamper-resistant hardware, which is often FIPS 140 certified. Using a Key Management System (KMS) alongside an HSM ensures secure key generation, storage and management; operating them separately can result in reduced security and increased operational complexity.
Where to use: tokenisation vaults, payment processing, signing operations, certificate issuance.
Pitfalls: storing keys in application code or environment variables; not backing up HSMs; neglecting hardware redundancy.
Quick test: do you use an enterprise KMS/HSM to generate and rotate keys? Are access controls and audit logs enforced on key operations?
Envelope encryption – Combine symmetric encryption of data with wrapping (encrypting) the data key using an asymmetric master key (stored in an HSM). This pattern allows rotating the master key without re‑encrypting all data.
Mobile app hardening
The OWASP Mobile Application Security Verification Standard (MASVS) establishes a foundation for mobile security. The 2024 MASVS v2.0 update streamlined redundant controls, introduced testing profiles, and added privacy profiles (MASVS-PRIVACY). This release aligns with the Mobile Application Security Testing Guide (MASTG) and introduces the MAS Workflows and Evidence (MASWE) project, which maps high-level controls to tests. For fintechs, implement MASVS Level 1 at minimum (basic environment checks), and then progress to Level 2 for critical services. Key controls include runtime application self-protection (RASP) to detect tampering and block attacks in real time; certificate pinning with backup pins; root/jailbreak detection; secure keystores (e.g., Keychain and Android Keystore); and device binding (linking user sessions to a specific device).
Pitfalls: ignoring root detection, storing secrets in app binary, neglecting in‑app communications encryption.
Quick test: does your app implement MASVS controls, detect tampering and restrict debugging? Are secrets stored in secure keystores and not hard‑coded?
Secure software lifecycle
Threat modelling and ASVS mapping – Begin by mapping your architecture, identifying data flows and classifying “crown jewels” (card data, personal identifiers, private keys). The OWASP Application Security Verification Standard (ASVS) provides a framework for testing web application controls and offers developers a metric by which to measure application security. The ASVS can be used as a metric, for guidance, or as a procurement requirement. Each requirement has a versioned identifier (v5.0.0-<chapter>.<section>.<requirement>) to facilitate referencing. Aim for Level 1 (basic) for general mobile/web applications and Levels 2 and 3 for sensitive financial endpoints. Map each ASVS control to a regulatory requirement. For example, injection prevention addresses ISO 27001 control A.14.2.3 and NIST CSF "Protect."
Static/dynamic/interactive testing (SAST/DAST/IAST) – Integrate static analysis into the CI/CD pipeline to identify insecure coding patterns prior to deployment. Use dynamic analysis to test running applications, including API endpoints and user interfaces. Use interactive testing for real-time instrumentation. Prioritize remediating high-severity findings and ensure that tests cover third-party dependencies. Implement software composition analysis (SCA) to track open-source packages and use a software bill of materials (SBOM) to inventory components. According to CISA's draft 2025 SBOM minimum elements, SBOMs provide a detailed inventory of software components, enabling organizations to identify vulnerabilities, assess risk, and make informed decisions. Adoption of SBOMs has grown, and machine-processable formats are needed to integrate them into cybersecurity practices.
Secrets management – OWASP's Secrets Management Cheat Sheet emphasizes the importance of centralizing and standardizing the handling of secrets. Since different teams consume secrets differently, the cheat sheet recommends that organizations centralize and standardize secrets management. This can be done using multiple solutions, and the purpose and location of each secret must be clear. Access control must adhere to the principle of least privilege. Engineers should not have access to all secrets, and fine-grained controls are necessary. Manual maintenance increases the risk of leakage, so automate secret management using a secrets pipeline, dynamic secrets, and automated rotation. Kubernetes patterns, for example, use a vault agent sidecar to deliver secrets to the application at runtime.
Where to use: API keys, database credentials, JWT signing keys, encryption keys.
Pitfalls: storing secrets in code or unencrypted configuration; not rotating secrets; poor audit logging.
Quick test: do you use a secrets manager with automated rotation and fine‑grained access controls? Are secrets removed from source code and CI/CD pipelines?
Check out a related article:
What Causes 95% of Cybersecurity Breaches - And How to Prevent Them
Software Supply Chain and Third-Party Risk - The Verizon Data Breach Investigation Report (DBIR) notes that 15% of breaches involve a third party, which is a 68% increase from the previous year. Build a third-party risk management (TPRM) program that identifies, assesses, and monitors vendors. According to Thomson Reuters, TPRM involves vendor selection, risk assessment, and continuous monitoring. Regulators can penalize companies for inadequate TPRM. Require suppliers to provide evidence of SOC 2/ISO 27001 compliance, perform penetration testing, and share incident reports. Maintain a software bill of materials (SBOM) and verify that suppliers responsibly manage vulnerabilities. Use frameworks such as NIST's Secure Software Development Framework (SSDF) and OWASP Dependency-Track for continuous monitoring.
Security chaos engineering & red teaming – Conduct chaos security drills that inject faults (e.g., certificate expiry, API latency, service drop) into your system to test your detection and recovery capabilities. Engage in periodic red‑team exercises to simulate real attackers and test both technology and human response.
Fraud defence and behavioural analytics
In addition to authentication, fintechs need fraud-detection engines to monitor behavior across sessions. Use a combination of velocity rules, behavioral biometrics, machine learning (ML) models, device intelligence, and mule detection to flag suspicious activity. Use 3-D Secure 2.x for card-not-present transactions. Dynamic challenge flows reduce friction while improving risk assessment. Integrate risk signals from open banking consents and account aggregation to detect unusual account linkages.
Zero‑Trust infrastructure and micro‑segmentation
The zero trust model assumes that there is no implicit trust within your network. Micro-segmentation divides networks into small, isolated segments with strict access controls. According to FileFlex, micro-segmentation prevents lateral movement by enforcing authentication, least privilege, and monitoring at granular levels. Zero Trust Data Access (ZTDA) applies these principles to file and folder access by requiring strong user and device authentication, the least amount of privilege necessary, and continuous monitoring. For cloud environments, implement identity-centric access control, micro-segmentation of workloads, just-in-time credentials, and CIEM/CSPM solutions.
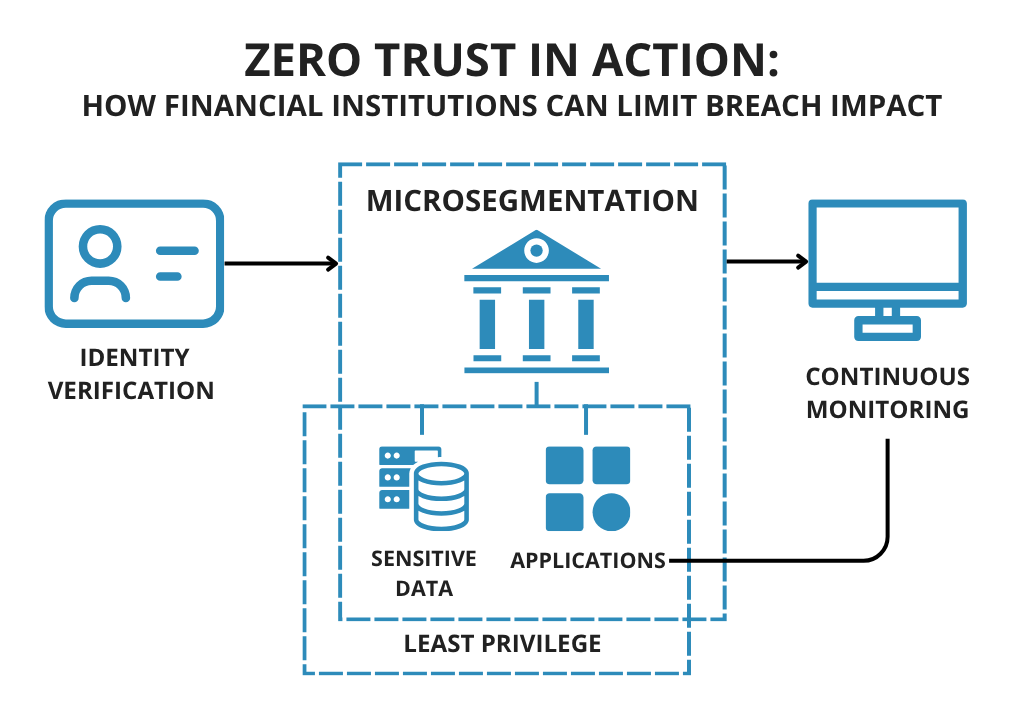
Third‑party & supply‑chain security
Include vendor due diligence in procurement: conduct risk assessments, review SOC 2/ISO 27001 reports, evaluate data‑handling practices and ensure data processing agreements (DPAs) include security obligations. Monitor vendors continuously—collect metrics, review their incident reports and ensure they notify you of breaches quickly. Use least privilege for integration—restrict API scopes and avoid long‑lived shared secrets.
Table A – Protocols and use cases
Compliance map: translate controls to regulations
Navigating multiple regulatory frameworks can be daunting. The following subsections outline key standards and how controls map across them.
PCI DSS 4.0
PCI DSS v4.0 took effect on 1 April 2024 and introduced 47 new requirements, many of which became mandatory after 31 March 2025. Key changes include:
- Encryption & anti‑malware – Organisations must encrypt stored sensitive authentication data and expand anti‑malware controls to protect systems beyond the traditional cardholder data environment. This means enabling endpoint detection and response (EDR) on servers and workstations.
- Vulnerability management – Increased emphasis on patching and vulnerability testing; companies must scan and remediate high‑risk vulnerabilities quickly and maintain inventories of assets and software.
- Access control & authentication – Multi‑factor authentication is required for all access into the cardholder data environment, not just administrators; minimum password length requirements are strengthened and periodic reviews of access privileges are mandated.
- Configuration management – Organisations must define and implement secure configurations for systems, network devices and applications, and monitor them continually.
DORA (Digital Operational Resilience Act)
DORA entered into application on 17 January 2025. It applies to banks, insurers, payment institutions, and critical ICT providers operating in the EU and aims to harmonise ICT risk management, incident reporting, resilience testing and third‑party oversight. Key obligations include:
- ICT risk management – Entities must implement risk management frameworks covering identification, protection, detection, response and recovery. This aligns with NIST CSF 2.0 functions (Identify, Protect, Detect, Respond, Recover, Govern).
- Third‑party risk – Financial entities must monitor and manage risk arising from ICT third‑party service providers, including cloud providers. Critical third parties will be supervised by European Supervisory Authorities.
- Digital operational resilience testing – Financial institutions must run penetration tests and vulnerability assessments, including scenario‑based testing.
- Incident reporting & information sharing – Significant cyber incidents must be reported promptly to regulators; DORA encourages sharing of threat information among institutions.
ISO 27001:2022
ISO 27001:2022 condenses the number of controls from 114 to 93, grouped into four themes: organisational, people, physical and technological. It introduces 11 new controls such as threat intelligence, information security for cloud services, and physical security monitoring. Organisations certified under ISO 27001:2013 must transition by 31 October 2025. Implementing ISO 27001 in fintech involves establishing an information security management system (ISMS) that covers policy, risk assessment, treatment plans, training and continuous improvement.
NIST Cybersecurity Framework 2.0
NIST’s updated CSF 2.0 adds a sixth “Govern” function to emphasise governance, supply‑chain risk and senior leadership’s role in cybersecurity. The framework now applies to all organisations, not just critical infrastructure. Fintechs should align their processes to the six functions:
- Identify – Asset management, business environment and governance.
- Protect – Access control, awareness and training, data security, maintenance and protective technology.
- Detect – Continuous monitoring, detection processes.
- Respond – Response planning, communications, analysis, mitigation and improvements.
- Recover – Recovery planning and improvements.
- Govern – Align cybersecurity with enterprise risk management, define roles and responsibilities, and oversee third‑party risk.
GDPR (EU) & Israeli Privacy Protection Law
- The General Data Protection Regulation (GDPR) establishes seven principles: fairness, lawfulness, transparency, purpose limitation, data minimization, accuracy, storage limitation, integrity and confidentiality, and accountability. Fintechs must establish lawful bases for processing data, obtain clear consent for new uses, minimize collection, ensure accuracy, and implement security controls.
- Amendment 13 to Israel’s Privacy Protection Law introduces sweeping reforms. The Knesset approved the amendment on August 5, 2024, and most provisions will take effect on August 14, 2025. Key elements include:
- Broader data definitions and sensitive categories – The amendment clarifies and widens the definition of personal data and sensitive categories.
- Mandatory Privacy Protection Officer (PPO) – Organisations engaging in large‑scale processing, systematic monitoring or operating as public authorities/data brokers must appoint a qualified PPO who reports directly to senior leadership and operates independently.
- Expanded transparency & consent requirements – Organisations must provide clear notices about data collection and use, ensure granular and explicit consent, particularly for sensitive data, and maintain auditable records of consent.
- Vendor risk and data transfers – Controllers must evaluate vendors’ privacy and cybersecurity practices, register databases used for data brokerage and comply with additional obligations when transferring data from the European Economic Area.
- Risk assessments and security obligations – Organisations holding large sensitive databases must conduct formal risk assessments and penetration tests at least every 18 months, document findings, update procedures and report incidents; non‑compliance can result in fines up to ILS 320 000 per violation.
Control‑to‑Standard mapping (Table B)
| Control | Standards satisfied | Evidence required |
| mTLS on all service‑to‑service paths | DORA (ICT risk management & third‑party risk), ISO 27001 (A.8 Communications Security), NIST CSF Protect, PCI DSS 4.0 (12.3) | Inventory of services; certificates and key management policies; pen‑test results showing authenticated connections. |
| Tokenisation & network segmentation for PAN/PII | PCI DSS 4.0 (reqs 3.4–3.6), ISO 27001 (A.8.2, A.8.3), GDPR (data minimisation & confidentiality), DORA | Token vault design, token mapping, segmentation diagrams, logs showing limited scope. |
| SBOM & SCA for software supply chain | NIST CSF Identify (ID.AM), DORA (ICT risk management & resilience testing), ISO 27001 (A.5.30 Supplier relationships), Israeli Amendment 13 (vendor risk) | SBOM outputs, vulnerability scans, supplier attestations, secure coding guidelines. |
| WebAuthn & RBA | PCI DSS 4.0 (multi‑factor & strong authentication), ISO 27001 (A.9 Access control), DORA (ICT risk management), NIST CSF Protect | Authentication policy, MFA logs, device binding records, risk scoring documentation. |
| Zero‑Trust micro‑segmentation | NIST CSF Protect (PR.AC, PR.DS), DORA (ICT risk & incident response), ISO 27001 (A.13 network security), Israeli Amendment 13 (risk assessments) | Network segmentation diagrams, identity‑centric access policies, continuous monitoring logs. |
| Secrets management & key rotation | PCI DSS 4.0 (reqs 3.5–3.6), ISO 27001 (A.10 cryptographic controls), NIST CSF Protect, GDPR (integrity & confidentiality) | Secrets manager configuration, evidence of automated rotation, audit logs, incident response procedures. |
Build vs buy: where startups burn time
Fintechs must decide which controls to implement in‑house and which to purchase. Building everything from scratch wastes precious runway. The table below summarises typical build/buy decisions.
| Domain | Best to buy | What you should build | Pitfalls |
| Identity (customer IAM) | Use managed identity platforms that support OIDC, OAuth 2.1, FAPI, WebAuthn, passkeys and step‑up MFA. They handle compliance (PSD2/SCA, PCI) and provide device intelligence. | Customise risk‑based policies (e.g., transaction‑level thresholds, step‑up triggers), consent UI/UX for open banking, and business‑specific flows. | Building identity from scratch results in insecure flows and delays; mismanaging MFA or risk scores frustrates users and invites fraud. |
| Payment & 3‑D Secure | Buy a compliant 3‑D Secure 2.x server with PSD2 SCA support; integrate with major card networks. | Build unique chargeback workflows and dispute management logic; integrate with ML fraud signals to decide when to challenge. | DIY 3‑D Secure may fail audits and cause transaction declines; not aligning challenge flows to risk increases friction. |
| Tokenisation & KMS | Use a dedicated token vault or third‑party tokenisation service with KMS/HSM; ensures PCI compliance and reduces scope. | Build wrappers around the vault for business logic, metadata and access control. | Storing tokens in your own database reintroduces PCI scope; not integrating HSM leads to weak key security. |
| Device intelligence & bot management | Buy device fingerprinting and bot detection services; vendors collect global telemetry to detect anomalies. | Build internal scoring algorithms combining vendor signals with proprietary behaviour data; tune risk thresholds for local context. | Over‑reliance on vendor risk scores may produce false positives; not protecting your API endpoints from bots opens path to ATO. |
| Logging/SIEM/SOAR | Purchase a cloud‑native logging and security information and event management (SIEM) platform with SOAR (security orchestration, automation and response) to aggregate events and automate response. | Build custom detection rules, correlation logic, and runbooks that map to your specific threat model. | Building a SIEM from scratch leads to poor scalability; not tuning detection results in alert fatigue or missed incidents. |
| Secrets management | Use a managed secrets manager or vault (e.g., AWS Secrets Manager, HashiCorp Vault). | Build integration code (sidecar, serverless functions) to deliver secrets to your services; enforce naming conventions and metadata tracking. | Storing secrets in config files or environment variables is a major risk; manual rotation causes outages. |
| Compliance reporting | Use governance, risk and compliance (GRC) tools to maintain control evidence, map controls to frameworks (PCI, ISO, DORA), and export auditor reports. | Customise metrics and dashboards; integrate with engineering tools to collect evidence automatically. | Not automating evidence collection leads to endless manual work; misalignment between controls and frameworks delays certifications. |
Implementation phases: MVP → scale
Every startup has limited resources. The following phased roadmap helps prioritise actions without boiling the ocean.
Phase 0: Threat model & baseline hardening (2–4 weeks)
- Conduct threat modelling & data inventory. Map data flows from client to API to data stores and third‑party services; identify crown jewels (payment data, personal identifiers, authentication secrets) and high‑risk scenarios.
- Baseline hardening. Implement TLS 1.2/1.3 with modern ciphers, enforce HSTS and disable insecure protocols; configure firewalls and API gateways to limit exposure; enable logs for all critical systems.
- Secret rotation & basic scanning. Use a secrets manager to store API keys, database credentials and encryption keys; set up automatic rotation; integrate static code analysis (SAST) and software composition analysis (SCA) tools.
Phase 1: MVP security (0–3 months)
- Adopt OAuth 2.1/OIDC with PKCE for all user authentication; implement FAPI 2.0 security profile for open banking flows including PAR/JAR, mTLS or DPoP.
- Introduce WebAuthn/passkeys for high‑risk transactions; ensure fallback to phishing‑resistant MFA (e.g., FIDO security keys or OTP via authenticator app). Implement risk‑based adaptive authentication and device binding.
- Tokenise sensitive data. Implement token vault for PAN/PII; use FPE if you need to preserve format; ensure keys are managed by a KMS/HSM.
- Mobile application security (MASVS L1). Apply basic protections: enforce certificate pinning with backup keys, detect jailbreak/root, use secure keystore, obfuscate code and integrate RASP for tamper detection.
- Logging & monitoring. Deploy a central logging platform; capture authentication events, API calls, errors and system metrics; define alert thresholds for unusual patterns.
- Vendor vetting. Conduct due diligence on any third parties, requiring SOC 2/ISO 27001 evidence; sign DPAs specifying security obligations; limit API access by scope.
Phase 2: Hardening (3–6 months)
- mTLS & micro‑segmentation. Implement mutual TLS for service‑to‑service communication, including microservices and database connections; segment network into isolated zones; enforce identity‑centric access control and just‑in‑time credentials.
- MASVS L2 & device binding. Upgrade mobile app to MASVS Level 2; enable device binding (linking session tokens to device keys) to prevent token replay; add advanced RASP features and runtime protections.
- ASVS L2/L3 for critical endpoints. Map each API endpoint to ASVS controls; integrate dynamic scanning (DAST/IAST) and pen‑testing; fix high‑severity findings. Generate SBOMs for every build and feed into vulnerability management.
- Vendor risk programme. Formalise TPRM: define onboarding questionnaires, risk scoring and continuous monitoring; maintain contracts with incident notification requirements; track fourth‑party dependencies.
- SBOM pipeline. Automatically generate SBOMs during the build process and store them; integrate with vulnerability feeds to detect component vulnerabilities; update components promptly when CVEs are published.
- Incident response & tabletop exercises. Develop incident response runbooks (see checklists below) and test them through tabletop exercises; align with Bank of Israel guidance requiring incident reporting and quantum readiness.
Phase 3: Scale (6–12 months)
- Zero‑trust micro‑segmentation & ZTDA. Deploy micro‑segmentation at network, application and data layers; adopt ZTDA to control file/folder access; use identity‑aware proxies and just‑in‑time credentials.
- SOAR & automation. Integrate your SIEM with SOAR to automate detection and response; build runbooks that orchestrate containment, ticketing and notifications; feed into metrics.
- Red teaming & continuous testing. Conduct regular red‑team engagements to simulate advanced attacks (phishing, lateral movement, supply‑chain compromise); implement bug bounty programmes to crowdsource vulnerability discovery.
- Backup & disaster recovery (DR) testing. Perform scheduled backups of databases and critical services; test restore procedures under simulated outages; maintain off‑site encrypted backups; ensure cryptographic keys used for backups are managed by HSMs.
- Continuous compliance & evidence automation. Use GRC tools to map controls to frameworks; automatically collect logs, test results and policies; produce evidence for PCI, ISO, DORA and Israeli audits.
Checklist 1: Go‑live readiness
- Threat model & data inventory completed (crown jewels identified).
- TLS/mTLS enforced across all public and internal interfaces.
- OAuth 2.1/OIDC with PKCE implemented; FAPI 2.0 for open banking flows.
- MFA & passkeys integrated; risk‑based authentication configured.
- Tokenisation vault live; encryption keys stored in HSM/KMS.
- Mobile app meets MASVS L1; RASP integrated; certificate pinning configured.
- Static/dynamic testing & SCA integrated into CI/CD; SBOM generated.
- Secrets managed via centralised vault; automated rotation set up.
- Logging & monitoring configured; alerts defined; on‑call rota established.
- Incident response plan drafted; roles and contact lists defined.
- Vendor risk assessments completed; DPAs signed; least‑privilege integration enforced.
- Compliance mapping produced; evidence prepared for PCI, DORA, ISO, GDPR and Israeli law.
Checklist 2: Incident playbook essentials
- Detection & triage – use SIEM/SOAR to detect anomalies; classify incidents by severity; verify if it affects payment data or personal data.
- Containment & eradication – isolate affected systems (e.g., revoke keys/tokens, disable compromised credentials); deploy patches; rotate secrets; block suspicious IPs.
- Communication – notify internal stakeholders (security, engineering, leadership, legal), external partners (payment networks, open banking partners), regulators and customers as required (DORA and PCI have strict timelines).
- Evidence collection & forensics – collect logs, memory dumps and network captures; ensure chain of custody; preserve data for law enforcement.
- Regulatory reporting – prepare reports for the Bank of Israel, Privacy Protection Authority (for Israeli data), European Supervisory Authorities (for DORA), card schemes (for PCI) and any other relevant regulators; include root cause, impact, remedial actions and future prevention.
- Customer notification & PR – draft clear, transparent communications; offer credit monitoring if required; coordinate with PR to manage messaging; update FAQs.
- Lessons learned & remediation – after containment, perform a post‑mortem; update threat models, patch management, training and vendor controls; integrate improvements into security roadmap.
Metrics that prove security is working
To convince leadership and investors that security investments pay off, track metrics aligned to business outcomes:
- Account takeover rate & reduction – monitor ATO attempts versus successful logins; the Sift data provides an industry benchmark of 2.5 % attack rate with 122 % YoY increase for fintech. Aim to maintain ATO rates well below industry averages.
- Frictionless authentication percentage – measure how many sessions complete without requiring step‑up MFA; increasing passkey adoption should raise this percentage while reducing ATO.
- MFA step‑ups avoided via risk scoring – track how many transactions are approved based on low risk without user friction; calibrate risk thresholds accordingly.
- Mean time to detect (MTTD) & mean time to contain (MTTC) – measure detection and containment times for high‑severity incidents; aim for minutes rather than hours.
- P0 vulnerability mean time to remediate (MTTR) – measure the time taken to fix high‑severity vulnerabilities discovered via SAST/DAST; integrate into engineering KPIs.
- Percentage of third‑party coverage – track vendors with completed risk assessments and ongoing monitoring; aim for 100 % coverage.
- Pen‑test findings trend – measure the number of high/medium findings decreasing over successive tests; require closure before production.
- Compliance gap closure – measure controls implemented versus required by PCI DSS 4.0, DORA, ISO 27001:2022 and Israeli law; close gaps proactively.
Israel & EU corner: local context
Israel’s Privacy Protection Law & Bank of Israel guidance
As noted, Amendment 13 modernizes Israel’s Privacy Protection Law. Israeli fintechs must:
- Appoint a Privacy Protection Officer if they process large or sensitive datasets
- Provide transparent notices and obtain explicit consent for sensitive data
- Evaluate vendors and register databases
- Conduct risk assessments and penetration tests at least every 18 months
- Be prepared for penalties of up to millions of shekels for noncompliance
Startups should incorporate privacy by design from day one by minimizing data collection, encrypting everything, tokenizing payment identifiers, and building consent management into the product.
The Bank of Israel has issued guidelines on quantum computing risks. Banks and payment service providers must raise awareness of quantum computing developments and integrate quantum risk considerations into supply chain risk management. They must also map encrypted information assets with their key lengths to plan migration to post-quantum cryptography. Israeli fintechs should ensure that their key management and crypto libraries support elliptic-curve algorithms and be prepared to adopt post-quantum algorithms as they become standard.
DORA implications for Israeli fintechs operating in the EU
Israeli companies that offer services to EU customers, such as payment institutions and e-money issuers, must comply with DORA. These companies must implement ICT risk management frameworks, conduct resilience testing, monitor third-party providers, and promptly report incidents. Coordinating with the Israel Privacy Protection Authority and EU regulators will be critical for cross-border data transfers. Adopting FAPI 2.0, mTLS, zero trust, and SBOM practices will help satisfy DORA and Israeli obligations.
Conclusion
Security is not a one-time exercise, but rather a continuous journey toward maturity. Startups often delay security measures until they achieve product-market fit, only to find themselves scrambling when regulators or partners demand proof of compliance. This playbook shows that the fundamentals—identity (WebAuthn, OAuth 2.1), API security (FAPI 2.0, mTLS), and data protection (tokenization, encryption, and key management systems (KMS))—can be implemented from day one. Compliance frameworks such as PCI DSS 4.0, DORA, ISO 27001:2022, NIST CSF 2.0, GDPR, and Israel's Amendment 13 can be mapped to specific controls and measured through automation.
As you build and scale your fintech company, approach security as you would product development: create a threat model, implement protocols, test, measure, and iterate. Focus on zero trust, microsegmentation, secrets management, SBOMs, and vendor risk. Use metrics to demonstrate progress, and adapt controls as threats evolve. Remember that regulation is not just about avoiding fines; it is a framework to protect your users, your brand, and the broader financial ecosystem.
If you need support implementing these protocols or aligning with international standards, our cybersecurity and fintech software development companies can help. We specialize in financial software development services with built-in security, ensuring that your minimum viable product (MVP) meets compliance standards from day one and can scale to bank-grade resilience. Contact us to learn how our AI and cybersecurity expertise can accelerate your journey.
Leave a Comment