Start-ups, scale-ups and established IT organizations all face the same challenge: delivering high-quality software quickly without compromising stability or security. A competitive edge is gained by teams that can launch features and resolve issues more quickly than their competitors. This is why DevOps is no longer just a buzzword; it is the backbone of modern software delivery.
DevOps combines cultural principles, toolchains and automated practices to bridge the gap between development and operations. When implemented effectively, it shortens release cycles, increases deployment frequency, and reduces failure recovery time. Research shows that organizations that embrace DevOps enjoy code deployments that are up to 46 times more frequent and recover from failures 96 times faster than those using traditional siloed approaches. Moreover, DevOps adoption isn’t limited to tech giants. By 2025, over 78% of organizations worldwide will have implemented DevOps practices, with nearly 90% of Fortune 500 companies having done so.
For start-ups, DevOps offers more than just speed. It provides a way to scale infrastructure efficiently, integrate security from the outset and iterate based on real-time user feedback. In this comprehensive guide, we will explore the five most important DevOps trends for startups and IT teams to watch in 2025, supported by data and examples.
A Brief History and the Cultural Imperative
The term 'DevOps' emerged in the late 2000s in response to the growing divide between development and operations teams. Inspired by agile and lean philosophies, the first practitioners emphasized shared ownership, shorter feedback loops, and continuous learning. Over the next decade, the rise of cloud computing, containerization and microservices turned DevOps from an experiment into a mainstream practice. Today, DevOps represents a toolkit and cultural movement that aims to break down silos and deliver value to customers faster.
Why Startups Need DevOps
Startups face unique pressures: they must move quickly, innovate continuously and earn customer trust while operating on tight budgets. DevOps addresses these needs by enabling rapid innovation, operational efficiency and scalable infrastructure. Through automation and collaboration, teams reduce manual overhead, shorten release cycles and handle growth without reinventing the wheel. Integrating security from day one (DevSecOps) mitigates risks early, while continuous monitoring and feedback loops ensure that products evolve based on real‑world usage. In short, DevOps is more than tooling - adopting it cultivates resilience and agility, positioning startups to compete with much larger firms.
Trend 1: Accelerating Time‑to‑Market and Innovation
One of the most common reasons why start-ups adopt DevOps is to accelerate releases without compromising on quality. In a world where customer needs are subject to rapid change, the ability to release features weekly - or even daily - can mean the difference between becoming a market leader and becoming obsolete. High-performing teams implement continuous integration and continuous delivery (CI/CD)pipelines, in which code is automatically built, tested, and deployed. According to recent DevOps studies, teams with mature DevOps pipelines deploy software up to 46 times more frequently and reduce lead time for changes by up to 90%.
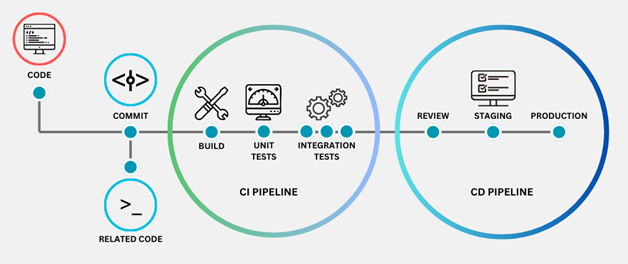
How Automation and CI/CD Drive Innovation
Modern DevOps pipelines are built around automation. Here’s how the pieces fit together:
- Source Control Management – All code resides in a shared repository (e.g., GitHub, GitLab). Developers create branches and open pull requests for peer review.
- Continuous Integration – Each commit triggers automated builds and test suites. Tools like Jenkins, GitHub Actions or GitLab CI compile code, run unit and integration tests and provide immediate feedback.
- Artifact Management – Successful builds produce deployable artifacts stored in artifact repositories (e.g., Nexus, JFrog Artifactory) for consistent deployments.
- Continuous Delivery – Automated pipelines deploy artifacts to staging and production environments using tools such as Argo CD, Spinnaker or AWS CodePipeline. Infrastructure definitions and configuration files ensure environments are reproducible.
- Monitoring and Feedback – Once in production, monitoring tools track performance and user behavior; feedback is fed back into the backlog for continuous improvement.
The beauty of this approach is automation eliminates manual bottlenecks. Teams can focus on building features rather than manually moving code across environments. For startups with limited personnel, automation is critical to scaling without expanding headcount.
Going Deeper: Continuous Delivery vs. Continuous Deployment
It is worth noting the distinction between continuous delivery and continuous deployment. With continuous delivery, your code is always in a deployable state. Automated tests validate each change, and while the release process is scripted, a human still approves the final deployment to production. Continuous deployment takes this one step further: every change is automatically deployed to production without manual intervention. Startups often begin with continuous delivery to build confidence in their pipeline, and as this grows, they transition to continuous deployment for faster iteration.
Microservices and Containerization
Many modern start-ups develop their products using microservices - small, independent services that communicate via APIs. This allows teams to deploy parts of their application independently, reducing the impact of each change. Containerization technologies such as Docker package code and dependencies into portable units, ensuring consistency from the developer's laptop to the production environment. When combined with orchestration platforms such as Kubernetes, containers enable horizontal scaling and self-healing, thereby reducing the risk associated with rapid deployment. DevOps practices complement microservices by automating the build and deployment of each service.
Best Practices for Implementing CI/CD
Adopting a CI/CD pipeline is more than setting up a tool; it’s about embracing best practices that promote reliability and maintainability:
- - build times, failure rates - and iterate. Encourage small, frequent commits rather than large, monolithic releases.
Common Challenges and How to Overcome Them
Teams should be aware of potential pitfalls, such as unreliable tests, complex pipeline scripts and cultural resistance. They should isolate tests, modularize pipeline code and integrate security checks early on (see Trend 3). Most importantly, foster a culture of continuous improvement. Training and quick wins can help to build trust in the automation process.
Trend 2: Infrastructure as Code (IaC) and Scalability
Infrastructure as Code (IaC) is the practice of defining infrastructure, such as servers, databases, networks and storage, in programmable, version-controlled files. Rather than clicking buttons in a cloud console, teams write configuration files (e.g. Terraform, AWS CloudFormation or Pulumi) that describe the required environments. When executed, the code provisions or updates infrastructure automatically.
Why Startups Need IaC
Startups often pivot and scale quickly. Manual infrastructure management can’t keep up with surging demand or sudden project changes. IaC offers several benefits:
Recent industry analysis notes that technology and financial sectors lead in DevOps adoption, with Fortune 500 companies approaching 90 % adoption rates and many of these adopters rely heavily on IaC. As cloud costs rise, more organizations use IaC to optimize resources, automate scaling and maintain compliance.
Examples of IaC in Action
- Global E‑commerce Platform: A medium-sized e-commerce start-up running on AWS needed to support holiday spikes. The company automated the creation of auto-scaling groups, load balancers, database clusters and caching layers using Terraform modules. During peak events, the environment scaled to support tens of thousands of concurrent users. This setup also enabled safe deployment of changes across staging and production environments, ensuring feature parity.
- Healthcare SaaS Platform: A SaaS provider serving medical clinics used Azure Resource Manager (ARM) templates to manage infrastructure across regions. The IaC approach ensured each clinic’s environment was compliant with data residency laws. When launching new clinic instances, the team executed ARM templates to deploy identical HIPAA‑compliant environments with encryption and network controls.
Declarative vs. Imperative IaC
IaC tools generally fall into two categories: declarative and imperative. Declarative tools, such as Terraform and CloudFormation, define the desired end state, and then determine the steps required to reach it. In contrast, imperative tools (such as Ansible or Chef) specify the exact sequence of commands to be executed. Declarative approaches are popular because they enable teams to describe infrastructure as a blueprint, making it easier to detect drift and achieve idempotence. Imperative tools are best suited to tasks involving configuration management across existing resources. Many organisations use a combination of the two: for example, Terraform might provision the infrastructure while Ansible configures the software on the provisioned servers. Understanding these paradigms helps teams to select the most appropriate tool for each task.
Best Practices for Adopting IaC
Implementing Infrastructure as Code requires discipline and planning. Consider these practices when embarking on your IaC journey:
- Modularize and Version: Break large configurations into reusable modules and track them in version control. Branches and pull requests ensure peer review and traceability.
- Test Infrastructure Code: Use tools like Terratest or kitchen‑terraform to validate modules before promotion. Automated tests catch errors before they reach production.
- Maintain Parity: Keep development, staging and production environments similar. Parameterize differences instead of creating entirely separate configurations.
- Protect Secrets and Detect Drift: Use secret management services rather than hard‑coding credentials, and periodically scan for drift using tools like Terraform Cloud or AWS Config.
- Document Decisions: Record why specific resources or modules were chosen. Documentation helps onboard new engineers and avoids future confusion.
Overcoming Challenges
Transitioning to IaC isn’t without obstacles: managing the state file is critical, large templates can become unwieldy and there is a learning curve for teams accustomed to GUIs. Adopt remote state backends, establish naming conventions, provide training and use policy‑as‑code tools to enforce governance. With these safeguards, IaC supports rapid scaling while keeping costs and risks under control.
Trend 3: Security Integration (DevSecOps)
Originally, DevOps focused on bridging development and operations. But security breaches, compliance requirements and privacy concerns have made security integration critical. Enter DevSecOps - a methodology that integrates security practices throughout the CI/CD pipeline. With DevSecOps, the question isn’t “How do we secure the application after deployment?” but “How do we embed security checks at every stage?”
Why Security Matters for Startups
For startups handling personal data, health records or financial transactions, security missteps can be catastrophic. Regulations like the General Data Protection Regulation (GDPR) and California Consumer Privacy Act (CCPA) require that user data is protected at all times. Moreover, startups often work with limited security expertise. Embedding automated security tools into the development pipeline helps catch vulnerabilities early, avoiding costly fixes later.
Key DevSecOps Practices
- Automated Static and Dynamic Analysis – Tools such as SonarQube, Snyk and Veracode perform static application security testing (SAST) during build stages and dynamic testing (DAST) during deployment. They flag vulnerabilities in dependencies and code.
- Software Composition Analysis (SCA) – SCA tools scan open‑source dependencies to detect known vulnerabilities and license compliance issues.
- Container Security – Container image scans (e.g., Aqua Security, Anchore) ensure containers don’t contain vulnerabilities or misconfigurations. Vulnerability scanning is integrated into CI pipelines.
- Secrets Management – Tools like HashiCorp Vault, AWS Secrets Manager and Kubernetes Secrets centralize sensitive credentials. Access is granted using short‑lived tokens rather than hard‑coded secrets.
- Infrastructure Security Scanning – Infrastructure as Code security analyzers (e.g., Checkov, Terrascan) check for misconfigurations in Terraform or CloudFormation templates.
- Compliance as Code – Automated checks ensure compliance with standards such as PCI DSS, HIPAA and ISO 27001, reducing manual audit overhead.
Building a Security‑First Culture
DevSecOps is as much about people and processes as it is about tools. In order to successfully integrate security, startups should foster a security-first mindset throughout the organization.
To cultivate this mindset, startups should focus on raising awareness, carrying out early checks and encouraging continuous learning. This can be achieved by providing regular training on secure coding and regulatory requirements, integrating security checks and threat modelling early in the lifecycle ('shift left') and designating security champions to spread best practices. Policies should be codified using frameworks such as OPA or AWS Config to enforce automatic encryption, tagging and multi-factor authentication. Finally, encourage ongoing education through webinars, capture-the-flag competitions and certification courses.
Threat Modeling and Risk Management
Threat modeling is a structured approach to identifying potential cyberattacks and designing countermeasures before incidents occur. Startups can adopt frameworks such as STRIDE (Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege) or PASTA (Process for Attack Simulation and Threat Analysis) to systematically analyze threats. Conducting threat modeling in the early stages of design helps teams prioritize controls, avoid design flaws, and prevent new features from introducing vulnerabilities. When combined with risk management practices, this proactive approach reduces the likelihood of security incidents and builds customer trust.
Security Tooling Selection Guide
Selecting security tools can feel overwhelming. Focus on three essentials: integration (the tool must fit into your CI/CD pipeline and support your languages), coverage (it should scan application code, infrastructure and third‑party dependencies) and actionable reports (providing clear remediation guidance without excessive false positives). For regulated industries, confirm that the tool supports necessary compliance reporting.
The Human Factor
Despite automation, humans remain central to security. Encourage open communication about security incidents without blame. Use blameless post‑mortems to learn from vulnerabilities and incidents. Recognize that perfect security is impossible; the goal is to reduce risk continuously and respond quickly when incidents occur. By nurturing a culture where security is everyone’s responsibility, startups can build robust defenses that grow with the company.
Trend 4: Outsourcing vs. In‑House DevOps
Despite rising adoption, lack of skilled personnel remains a barrier to full DevOps maturity. Building an in‑house DevOps team requires sourcing senior engineers proficient in Kubernetes, Terraform, cloud platforms and CI/CD tooling. This process is costly and time‑consuming, and it can delay the very agility that DevOps promises. As a result, many startups explore managed DevOps services or DevOps as a Service models to accelerate adoption without the overhead of hiring an entire team.
Pros and Cons of In‑House DevOps
| Aspect | In‑House DevOps | Comments |
| Control & Customization | High – teams can tailor pipelines to exact needs. | Requires strong internal expertise. |
| Cultural Alignment | Integrated with organizational values. | Requires time to develop cross‑functional collaboration. |
| Cost | Higher upfront cost (salaries, benefits, tooling). | Costs may be justified for large, complex products. |
| Scalability | Limited by team capacity. | Hiring and training take time. |
Pros and Cons of External DevOps Services
| Aspect | External DevOps Services | Comments |
| Expertise | Immediate access to senior talent and best practices. | Providers handle recruiting and training. |
| Speed | Faster deployment of pipelines and environments. | Onboarding can be quicker than hiring new staff. |
| Cost | Lower overhead compared to building a full team. | Predictable monthly pricing. |
| Flexibility | Scale services up or down based on project needs. | Some loss of direct control; success depends on communication. |
When to Choose External DevOps Services
- Early‑Stage Startups: When speed to market is critical and resources are limited. Outsourcing accelerates the setup of reliable pipelines.
- Scaling Companies: When launching new products or expanding into new markets. A DevOps partner can help scale infrastructure quickly.
- Limited In‑House Expertise: If existing teams lack DevOps skills, external specialists can implement best practices while upskilling internal staff.
Factors to Consider When Evaluating External DevOps Partners
The decision between in-house and external DevOps support isn’t purely financial. Startups should evaluate potential partners based on several factors:
Focus on expertise and cultural fit, security and compliance, customization and knowledge transfer, and pricing transparency. Look for providers who are experienced with your technology stack, communicate well, follow secure practices, tailor solutions rather than offering one-size-fits-all, and willingly share knowledge. Compare pricing models (retainer versus pay-as-you-go) to ensure they align with your growth plans.
What to Outsource and What to Keep In‑House
Even when hiring outside specialists, startups should maintain ownership of their product vision and core intellectual property. One common approach is to outsource the technical aspects while maintaining ownership of the overall design. Consider the following guidelines:
Use external specialists for standardized tasks, such as infrastructure provisioning, CI/CD pipeline setup, and environment monitoring. These areas benefit from scale and deep experience. These tasks are ideal candidates for DevOps outsourcing when internal capacity is limited. Retain ownership of your product’s architecture, feature roadmaps, and domain-specific algorithms. These elements are central to your value proposition. Collaborate with partners for security design and policy - they can offer expertise, but your team must understand and own the posture.
Hybrid Models and Knowledge Sharing
A hybrid approach is common - external specialists set up the initial pipelines and infrastructure, then hand over operations as your team grows more capable. To succeed, insist on comprehensive documentation, runbooks and training. Pair internal developers with external DevOps engineers to transfer skills and build confidence.
Performing Due Diligence
Before signing with a provider, review contracts carefully (SLAs, exit terms), verify their security practices and ask for references. Pilot a small engagement before committing to a long‑term contract. Treat vendors as collaborators rather than outsiders - the goal is to accelerate growth without compromising control or security.
Trend 5: Continuous Monitoring and Feedback Loops
DevOps isn’t just about deploying faster. It’s about ensuring software remains reliable, performant and secure in production. Continuous monitoring provides visibility into systems and applications, allowing teams to detect anomalies, resolve issues quickly and glean insights from user behavior. According to DevOps research, organizations that adopt monitoring and feedback as part of their DevOps practice see significant improvements in uptime and customer satisfaction.
Key Monitoring Pillars
- Application Performance Monitoring (APM) – Tools like Datadog, New Relic and AppDynamics measure request latency, throughput, error rates and user experience metrics. APM helps identify bottlenecks in code or infrastructure.
- Infrastructure Monitoring – Metrics from servers, containers, databases and networks (CPU, memory, disk I/O) provide health checks. Tools such as Prometheus, Grafana and CloudWatch capture and visualize data.
- Log Aggregation and Analysis – Centralized log platforms (e.g., ELK Stack, Splunk) collect logs from multiple services. Correlation and search tools help troubleshoot issues quickly.
- Real‑Time Alerting – Alerting systems notify on‑call engineers of anomalies and outages via Slack, email or PagerDuty. Alert policies are tied to SLAs and SLOs.
- User Feedback Integration – Post‑deployment, teams gather customer feedback via analytics tools, surveys or user sessions. This data feeds back into the development cycle to improve features.
Monitoring vs. Observability
Monitoring tells you when something is wrong; observability helps you understand why. Observability is achieved when you can answer unanticipated questions about your system’s state without adding new instrumentation. It relies on three pillars - metrics, logs and traces - captured in a way that allows engineers to follow a user request across services, identify anomalies and pinpoint root causes. As systems become more distributed (think microservices and serverless functions), observability becomes indispensable. Modern tooling (e.g., OpenTelemetry, Jaeger, Zipkin) supports collecting distributed traces and correlating them with logs and metrics.
Instrumentation and Data Collection
To gain insights, you must instrument your code and infrastructure. Instrumentation means adding hooks that emit metrics (e.g., request counts, error rates), logs (structured events with context) and traces (spans showing the journey of a request). Adopt open standards like OpenTelemetry, tag data consistently (service name, environment, region), and leverage automated instrumentation provided by frameworks. In high‑traffic services, apply sampling strategies to balance visibility with storage costs.
Check out a related article:
What is the Difference Between QA, QE, and QC?
Best Practices for Effective Monitoring
Effective monitoring goes beyond installing a tool. Start by defining service level objectives (SLOs) that translate customer expectations into measurable targets. Create runbooks and centralize dashboards so that teams know how to respond and share a single source of truth. Monitor business metrics alongside technical ones to understand the customer impact of outages. Finally, collect user feedback continuously through analytics and surveys; this qualitative data informs product roadmaps as much as technical metrics do.
Observability in Action
Consider a logistics startup with a fleet management platform. When users reported sporadic delays in tracking shipments, engineers used distributed tracing to follow requests across microservices. They discovered that a third‑party API call intermittently timed out, causing cascading delays. After instrumenting retries and caching, the issue disappeared. Without observability, the problem would have been difficult to reproduce.
Feedback Loops and Continuous Improvement
Monitoring and feedback loops close the DevOps cycle. These loops allow teams to measure the impact of changes, learn from real-world usage, and quickly adjust. Use the data to prioritize features, deprecate unused components, and optimize performance. Share these insights with everyone in the organization, including developers, product managers, customer support, and leadership, so that everyone understands how technology decisions affect customers.
Challenges and Mitigations
Implementing effective monitoring can be challenging. Avoid alert fatigue by tuning thresholds and aggregating related alerts. Break down data silos by integrating metrics, logs and traces. Manage costs through retention policies and sampling, and respect privacy laws by anonymizing user data. Addressing these issues proactively helps build monitoring systems that support scalability and customer happiness.
Conclusion - Choosing the Right DevOps Path
The five trends discussed - accelerated time‑to‑market, Infrastructure as Code, security integration, outsourcing vs. in‑house, and continuous monitoring - represent the top concerns for startups adopting DevOps in 2025. Together, these trends form a cohesive roadmap for building modern, resilient software delivery pipelines.
DevOps adoption has skyrocketed, with 78% of organizations globally embracing it, and nearly 90% of Fortune 500 companies adopting it. The benefits are tangible: Deployments are 46 times more frequent, lead times are 90% shorter, and recovery from failures is 96 times faster. Beyond the metrics, DevOps offers cultural and operational transformation. It encourages experimentation, breaks down silos, and fosters ownership across the product lifecycle. Startups can innovate quickly, scale reliably, and maintain customer trust by implementing DevOps principles.
The trends we explored are interconnected. Accelerated delivery depends on robust infrastructure automation and security practices. Infrastructure as Code provides the foundation for consistent environments and scalable systems. DevSecOps embeds security into every stage, rather than adding it on at the end. Partnering with external DevOps teams offers access to expertise while your team learns and grows. Continuous monitoring turns customer usage into actionable insights, closing the loop. Together, these practices create a cycle of continuous improvement, learning, and innovation.
Practical Takeaways
- Automate Everything You Can: Set up CI/CD pipelines with automatic testing, building and deployment. Use containerization to ensure consistency.
- Use IaC to Scale and Stay Compliant: Adopt Terraform or CloudFormation to manage infrastructure like code and maintain consistent environments.
- Integrate Security Early: Incorporate SAST, DAST, container scanning and secrets management into your pipelines. Compliance should be part of the pipeline, not an afterthought.
- Evaluate External vs. Internal Needs: If speed and expertise are critical and hiring is a bottleneck, consider working with a managed DevOps service provider for predictable costs and faster setup. For companies with unique requirements and long‑term capacity, building an internal team offers greater control.
- Monitor Continuously: Deploy robust monitoring, alerting and feedback loops. Use metrics and user feedback to continuously improve your product and infrastructure.
- Invest in Training and Culture: Encourage cross‑functional collaboration. Provide training on DevOps tools, agile methods and security practices. Remember that tooling alone cannot succeed without a supportive culture.
- Adopt Observability and User Insights: Instrument your applications to collect metrics, logs and traces. Combine technical telemetry with user feedback to prioritize features and fix pain points.
- Treat DevOps as a Journey: Transformation doesn’t happen overnight. Start small, iterate and celebrate milestones. Use retrospectives to learn from successes and failures.
At Intersog, we’ve helped startups across healthcare, fintech, e‑commerce and AI to implement these trends effectively. Our DevOps engineers specialize in designing automated pipelines, building Infrastructure as Code environments and embedding security into every step. Whether you’re launching your product or scaling globally, we can provide tailored solutions from managed DevOps engagements to coaching your team.
Ready to accelerate your software delivery and innovate with confidence? Visit Intersog’s DevOps Services to explore how our team can help you harness the power of DevOps in 2025 and beyond.
Leave a Comment